SHA1 Root causing PCI Failure
As anyone who manages an e-commerce website will know, getting your website PCI compliant can be a bit of a pain especially when that yearly report gets sent over flagging a number of complicated issues to fix.
With the Nimbus Hosting platform, we've tried to make this process easier by adding the ability to make your website PCI compliant with just one click. For more information about this, see here.
One issue we've noticed recently if that even if your website has PCI compliance enabled in our platform, certain payment gateway providers will flag issues with the SSL such as the below:
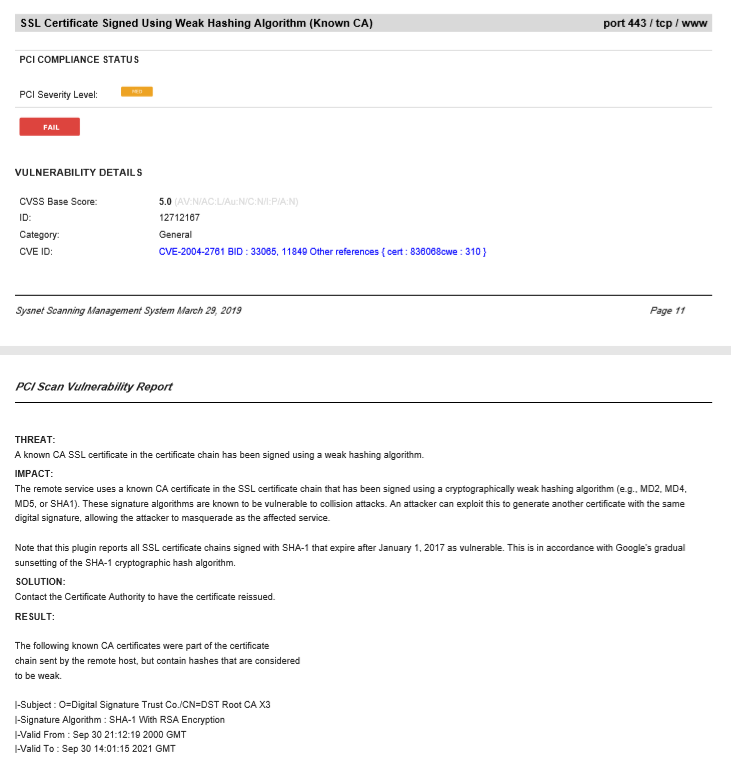
If you look closely at the report the problem they have flagged is with one of the chain certificates rather than the SSL itself:
|-Subject : O=Digital Signature Trust Co./CN=DST Root CA X3
|-Signature Algorithm : SHA-1 With RSA Encryption
Part of the chain is using a SHA-1 root and that's why the scanner has flagged this as a security issue. SHA-1 is indeed something that is no longer secure however when it comes to SSL's and the encryption being used from your browser to the website, the Root certificate doesn't actually play a part in how the traffic is encrypted. Therefore it's actually just the payment gateway provider being overzealous with their scan and you'll likely need to raise an exception for this with your payment gateway provider for this issue in order to pass PCI.
We've seen this with both Safer Payments and Trustwave and there's quite a lot of info online about clients who use LetsEncrypt that also need to be PCI compliant.
Sources:
https://www.entrustdatacard.com/blog/2014/april/need-sha-2-signed-root-certificates
https://community.letsencrypt.org/t/pci-compliance-sha1-root/55097
Updated 7 months ago
